A New Era of Security: Saying Goodbye to the Data Center Perimeter18 min read

We’re about to have a different kind of conversation here on this blog. We’re not discussing airflow or rack density. We’re going to talk about security and why it matters to every data center and IT professional.
Let’s start here: You. Are. A. Target.
In a connected economy, malicious actors are getting exceedingly creative in obtaining information and data from your data center walls. Adversaries are no longer lone wolves but have become a community trying new techniques, trading intellectual property, and sometimes working together. Most importantly, the speed of attacks has accelerated. Many now attack in days or hours, while it may take months or years for victims to discover they’ve been breached.
Finally, and this is the crucial part, every organization directly encounters malicious content or actors. While most interactions do not result in harm, adversaries do not lack opportunity.
The Perfect Cybersecurity Storm
I’m sure you’re not surprised by this, but 2020 created some massive headaches for security professionals. Workers who never in their dreams thought they’d be persistently working from home are now looking at this setup as a permanent situation. And the numbers reflect this change. The use rate of particular collaboration and videoconferencing tools has been exceptionally high. Cisco Webex usage has increased by 600%, Zoom by 350%, Microsoft Teams by 300%, and Slack by 200%.
On the security front, phishing attacks have increased by over 600% throughout 2020. Furthermore, these attacks have become supercharged and even AI-driven. Consider this:
- 94% of threats come through the inbox
- AI will conduct automated social media reconnaissance
- Phishing attacks will become contextualized and seem genuine
- Victims will be more easily lured
According to a study by Deloitte, COVID-19 was a force accelerator and perfect storm during 2020 for insiders to put data at risk. Employees are 85% more likely today to leak files than they were pre-COVID. It doesn’t get any better when you incorporate highly risky behavior by the user.
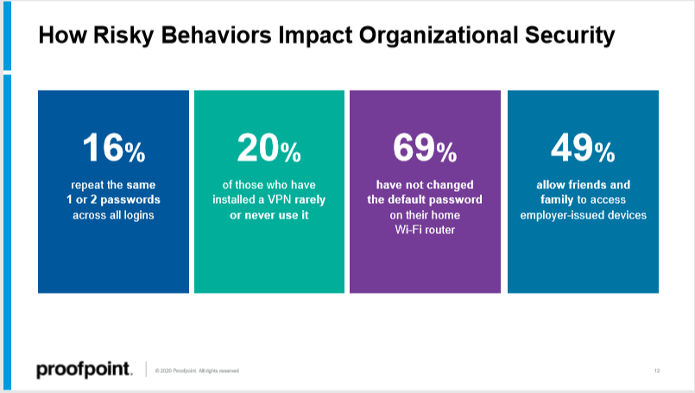
With this in mind, let’s bring in the data center professional and remind everyone why this is all so important to consider. For the first time, the latest AFCOM State of the Data Center Report dove into the topic of zero trust and how it impacts our data centers. (Be sure to join me for the free, live event, where I present more of these findings!) Here’s a sneak peek into the results:
As it relates to the top security and infrastructure threats, consider the following:
- Ransomware: 59%
- Outside threats (human): 52%
- Loss of PII (personally identifiable information): 43%
- Advanced Persistent Threats (theft of IT and corporate data): 43%
- Insider threats (human): 42%
- DDoS: 34%
- Inadequate or non-existent business or disaster recovery plan: 29%
Many leaders are finally looking beyond traditional security walls and working to understand better their users and the data they access. Ensuring that you create a good security posture means taking on a layered approach to security. Things like ransomware not only impact your systems but potentially your customers as well. Be aware of this, and segment and protect your data.
Here’s another point: DDoS attacks have been growing in size and ferocity. For example, the FBI is alerting healthcare technology leaders to the rise in DDoS attacks against their most critical health service systems. This is something to be aware of as you design your connectivity and telecommunications architecture. DDoS scrubbing solutions and protection can help you mitigate DDoS threats.
Interestingly, that second trend around outside human threats is a genuine concern. A recent article on Data Center Knowledge dives into a foiled AWS data center bombing plot. Targeting data centers is a new development. Experts believe the incident should spur review of physical security posture, investment in dark-web monitoring.
Zero Trust and the Data Center
Developed in 2010 by John Kindervag, who was a principal analyst at Forrester Research, zero trust technologies are actively (and finally) moving into the mainstream. Without a doubt, digital infrastructure security will need to be redefined in 2021 and beyond.
This includes physical security and logical security, where we ensure data integrity, applications, and services. The model behind zero trust is centered on the idea that organizations should not automatically trust anything inside or outside its perimeters. Instead, the model instructs security, data center, and network professionals to verify anything and everything trying to connect to its systems before granting access.
Goodbye Perimeter, Hello Contextual Security
To replace traditional perimeter-focused security architectures, leaders in the IT and business world turn to zero trust. Leveraging this type of model allows security and technology professionals to ensure that both security and access decisions are persistently and dynamically enforced based on critical criteria. This includes the person’s identity, where they’re coming in from, the device they’re using, and even granular user context variables.
Another critical point is that zero trust architecture explicitly dictates that only authorized and authenticated devices, users, and systems can access services, applications, and data. This model protects those same applications and data points from new and advanced threats on the internet in parallel.
When working with zero trust, you’re really deploying a least access principle. The architecture allows IT to offer each user or service access to particular applications and data sets. This means that security professionals no longer have to sweat it out over fears of providing too much access. This works great with customers, partners, suppliers, end-users, temporary workers, and so on because the access model can be tightly controlled and tailored around particular access criteria.
The basis of zero trust revolves around data authentication. Remember the earlier mentioned increase in video and teleconferencing solutions? The reality is that users, endpoints, email, cloud applications, and conferencing solutions have all become attack vectors and targets. With zero trust, you’re designing a model where you simply cannot trust anyone or any device. You’re reshaping the concept of a “perimeter” by adopting new levels of data protection with smarter authentication tools. This is why, as part of a zero tryst adoption process, security and IT leaders must have a very clear understanding of their applications, users, data sets, access methodologies, technology assets, and more. This needs to be understood before any zero trust architecture is deployed.
Why This Matters for a Distributed Workforce
A new Gallup study found 56% of U.S. workers were “always” or “sometimes” working remotely in January. The percentage of workers punching in from home hit a high of 70% in April. A similar survey last year found that only about 10-20% of respondents indicated that they were sometimes or always working from home consistently.
This is an essential consideration because zero trust is not at all dependent on location or even traditional perimeter security designs. This is why you can’t effectively enforce a zero trust architecture in one location. Instead, the design and concept must be proliferated through an entire technology and business ecosystem. Basically, the right users need to have access to the right applications, services, and data.
As a final thought to you, the data center or technology leader reading this, please take all of this advice and apply it contextually to your business. Zero trust is not just one piece of technology or a really cool piece of software. It really is an entire architecture, approach, toolset, and business mindset. On that note, changing user behavior and conducting awareness training is a big part of zero trust. A recent study from Webroot found that after 12 months of ongoing phishing simulations and security awareness training courses, end users are 70% less likely to click through on a phishing message. Remember, more than 90% of new and emerging threats are coming in through your inbox.
With our perimeters quickly changing into a much more distributed model, it’s time to take a similar approach to security in an era of zero trust.
Real-time monitoring, data-driven optimization.
Immersive software, innovative sensors and expert thermal services to monitor,
manage, and maximize the power and cooling infrastructure for critical
data center environments.
Real-time monitoring, data-driven optimization.
Immersive software, innovative sensors and expert thermal services to monitor, manage, and maximize the power and cooling infrastructure for critical data center environments.

Bill Kleyman
Industry Analyst | Board Advisory Member | Writer/Blogger/Speaker | Contributing Editor | Executive | Millennial
Bill Kleyman is an award-winning data center, cloud, and digital infrastructure leader. He was ranked globally by an Onalytica Study as one of the leading executives in cloud computing and data security. He has spent more than 15 years specializing in the cybersecurity, virtualization, cloud, and data center industry. As an award-winning technologist, his most recent efforts with the Infrastructure Masons were recognized when he received the 2020 IM100 Award and the 2021 iMasons Education Champion Award for his work with numerous HBCUs and for helping diversify the digital infrastructure talent pool.
As an industry analyst, speaker, and author, Bill helps the digital infrastructure teams develop new ways to impact data center design, cloud architecture, security models (both physical and software), and how to work with new and emerging technologies.
Really informative read, Bill! Zero trust works on the principle of “always verify and never trust” rather than the tradition of “trust but verify”. With greater visibility into the system combined with predictive and behavioral analytics, you can effectively apply security policies, enforce compliance, and reduce risk.